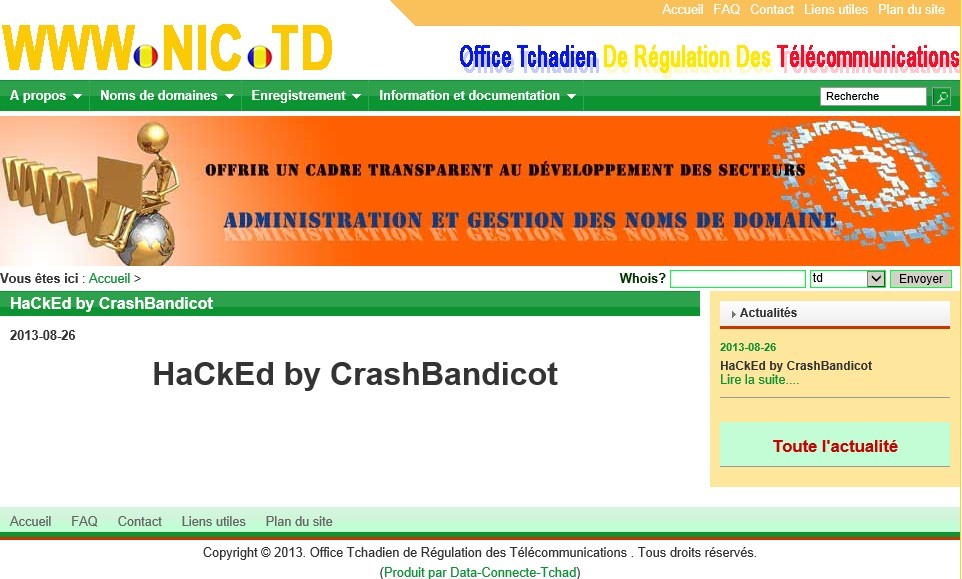
9-21日,在.TD域名的管理机构,www.nic.td 查询域名时 ,发现有条不显眼的标题 “HaCkEd by CrashBandicot”。
一个国家顶级域名的管理机构被入侵,很显然,还是让人感觉不错的~ 。。。
顺便在 Bing 查下这 “HaCkEd by CrashBandicot”。 还查到不少被他们改页面的站点。
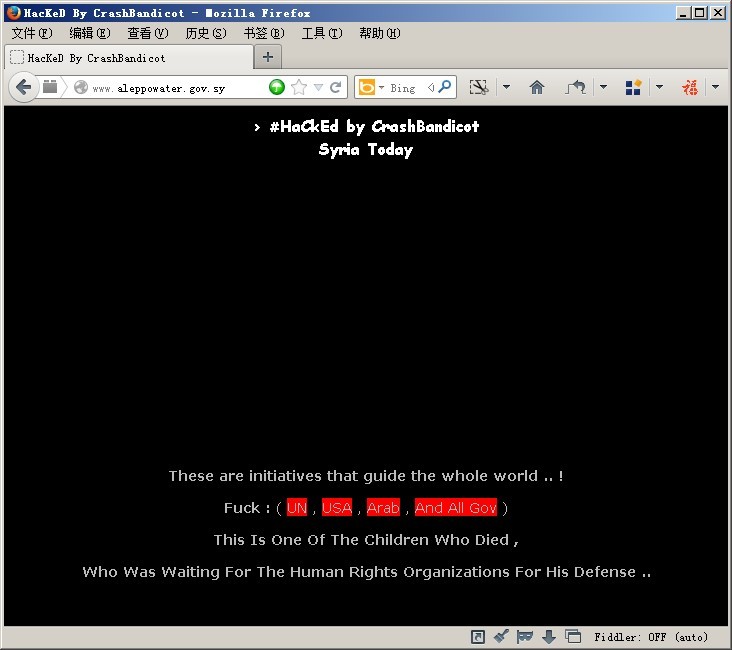
这个就是地处主要战场的阿勒颇,阿勒颇的水x局?! 我宁可相信这是域名劫持, 很难相信叙利亚一个政府网站会放在一个美国主机
http://bohu.net/dns/?doquery=1&question=www.aleppowater.gov.sy&type=A&server=8.8.8.8&port=53
www.aleppowater.gov.sy has IPv4 address: 66.63.181.105(美国加利福尼亚州洛杉矶QuadraNet网络公司)
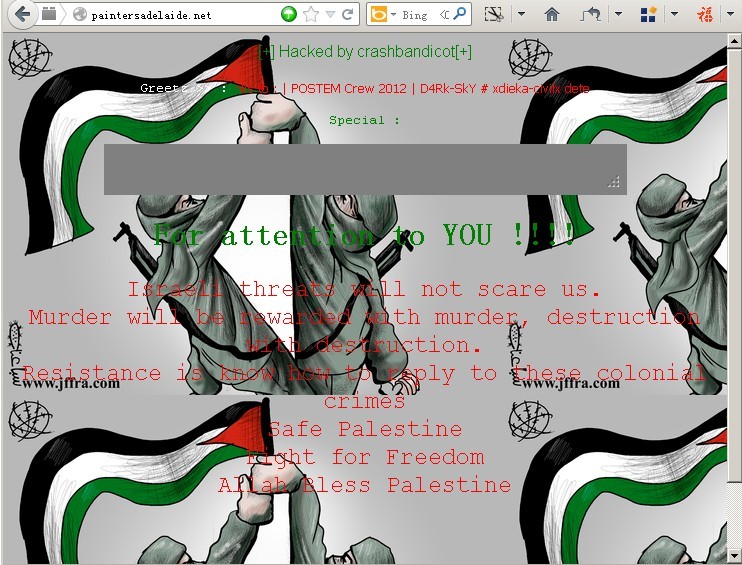
下面这个图文声色,做工精美,特别是背景音乐还是不错的。(MP3: http://www.4shared.com/embed/412420232/f5ca175c)
http://bohu.net/dns/?doquery=1&question=paintersadelaide.net&type=A&server=8.8.8.8&port=53
paintersadelaide.net has IPv4 address: 103.9.169.121(澳大利亚)
“CrashBandicot”应该是中东的穆斯林黑客团体(Muslim Hacker )所为,更具体可能为巴勒斯坦或亲叙利亚政府的黑客,他们标榜和宣扬自己的muslim hacker身份,并为此自豪。看到一个留有网站“crash-bandicot.co.cc”, 但是无内容。
Bing | Google 一下,还有不少:
www.aru-edu.com,kasbah-sable-dor.net,world-of-empathy.org,www.cadumotos.com.br
。。。 。。。
。。。
竟然还有一中国政府网站 bm.ml.gov.cn , 这个应该是注入进入的,没改首页藏的很深。
最后在 http://evuln.com/labs/hackedby/1882/ 看到一个清单:
eVuln Labs. The list of websites with the following signature:
# Hacked By CrashBandicot #
Discovered Website Hoster 2013-07-25 ***osalvomendes.com.br 2013-06-16 ***osalvomendes.com.br dialhost.com.br 2013-01-15 ***ordios.com 2013-01-12 ***ld-of-empathy.org ispfr.net 2013-01-10 ***internacional.com smart-hosts.net 2013-01-06 ***theredge.com weatheredge.com 2013-01-03 ***ehpraise.com 2012-12-24 ***juvenilalianzacri stiana.org smart-hosts.net 2012-12-24 ***bridgeconstructio n.co.uk justhost.com 2012-12-24 ***ica.fr kundenserver.de 2012-12-19 ***kmakerenemy.com bookmakerenemy.com 2012-12-19 ***hura.org lunarpages.com 2012-12-19 ***-account.com 2012-12-18 ***ejan.com ispfr.net 2012-12-18 ***ionalachieverscon gressbonus.com justhost.com 2012-12-18 ***ear.net cluster010.ovh.net 2012-12-18 ***webblog.com 2012-12-18 ***imuktaxback.com justhost.com 2012-12-18 ***klascoop.net 2012-12-18 ***thingvillage.com extendcp.co.uk 2012-12-18 ***dengarage.co.uk justhost.com 2012-12-18 ***fitswebdesign.co.uk justhost.com 2012-12-18 ***hatvnova.com 2012-12-18 ***aciznatury.com justhost.com 2012-12-18 ***ances-privees.com 2012-12-18 ***skiprawniklondyn. co.uk justhost.com Total 27 websites
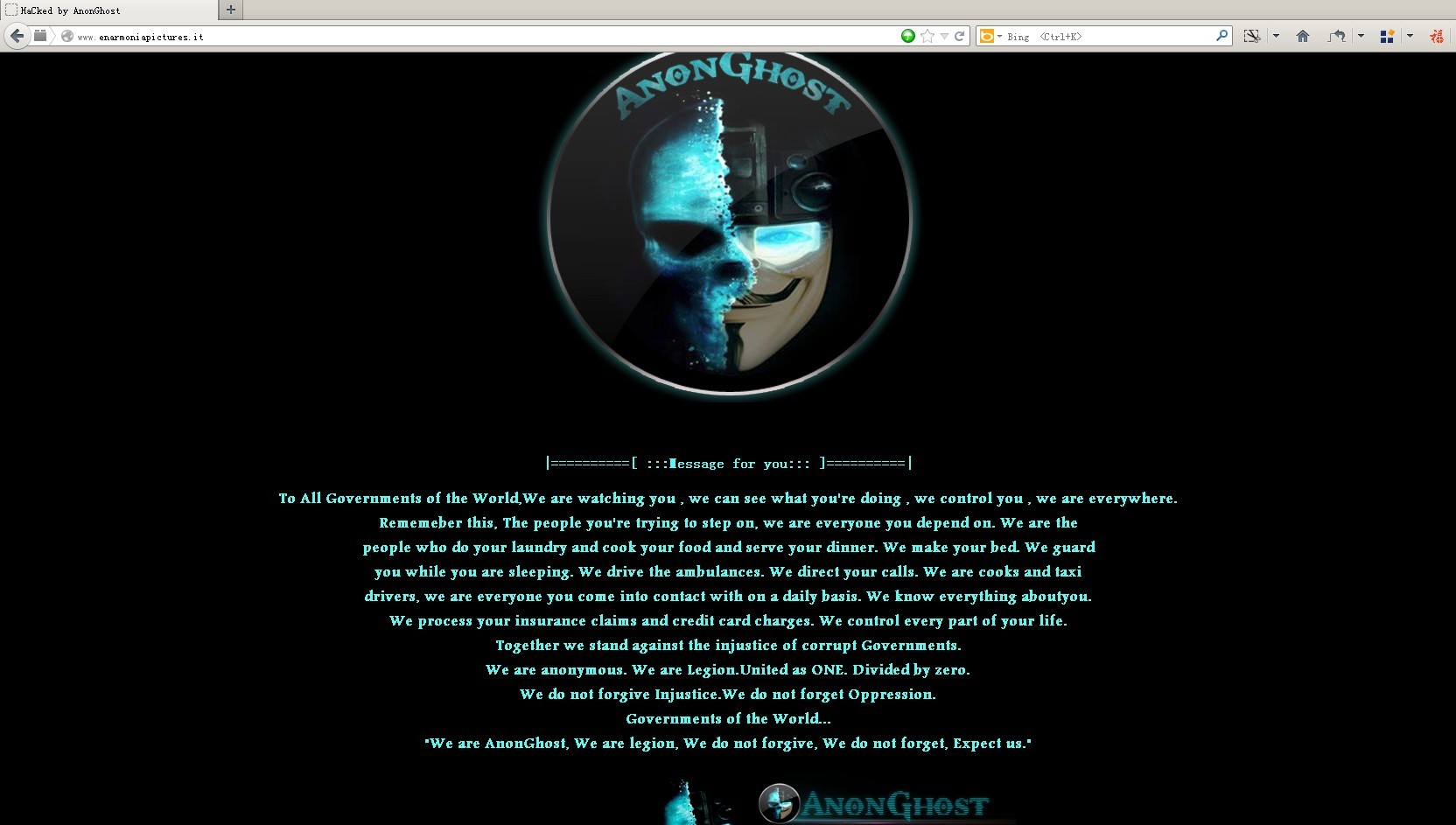
看了 eVuln Lab 的统计列表,才知道 “CrashBandicot” 只是个小喽啰。 大神是 “AnonGhost”,有自己公开的网站www.anonghost.com ,以反以著称。
Latest most active defacers.
Websites defaced Signature 1295 HaCked by AnonGhost 747 Hacked By International Force 678 Hacked By Dark Knight Sparda 563 Hacked By ReZK2LL Team 202 HACKED BY KRAD XIN 100 Hacked By # brkod # aLsha67 88 ҳ̸Ҳ̸ҳ Hacked By Maniak k4sur ҳ̸Ҳ̸ҳ 84 Hacked By.White Hat 83 Hacked By Afghan Cyber 72 Hacked By RooT HaXor 68 .:: Hacked By : T3RMiNaL 63 Hacked By Afghan Cyber Army 62 HacKed By Jack Riderr [ Johor Hacking Crew ] 62 hacked by saif ule est, web sniper, saif ule est 52 HackeD By h4x0r HuSsY 47 hacked by VIRTUAL 35 hacked by Sa-Dz 34 Hacked by Kosova Warriors Group 32 Hacked By Lionel MajDii 30 HackeD By Crack kid 29 Hacked by Panda Dot ID 28 Hacked by Dr.SaFa7 & Shi6an 7rb kuwait hackers 26 —==[ Hacked By ALFA TEaM ]==— 23 Hacked by Krad Xin RSS Feed 23 Hacked By 3xp1r3 Cr4Ck 20 Hacked by LORDOFDARKNES 14 Hacked by WaRLoCK 13 hacked by w7sh.syria 13 Hacked by Hank Sandlep 13 Hacked By .. brkod 11 hacked by Amirh03in 10 Hacked By NightMare 10 Hacked by xLitleonZ
HaCked by AnonGhost 的“作品”赏析:
等等 。。。 。。。 (Bing 、 Google 自己搜吧)
 CSV
CSV Plain text
Plain text